SQL Injection is one of the most ordinary and perilous web vulnerabilities within the field of cybersecurity. If you deal with web applications, protection from SQL Injection is what will provide your users’ data and your own reputation in security. In simple words, SQL Injection happens when an attacker injects malicious SQL code into a query to modify it so that it may gain unauthorized access, and modify, or delete sensitive information. This is one of the greatest threats that can happen in any system containing SQL databases and user input, so it appears at a pretty high spot in the developer community as well as that of security teams.
Real-World Impact of SQL Injection
SQL Injection attacks have been successful in some of the most recognized companies in the world. It actually led to major data breaches and monetary loss. For instance, hackers exploited a SQL injection vulnerability in 2015 during an attack on the UK telecommunications company TalkTalk, compromising the sensitive information of thousands of customers. Such incidents emphasize the need to understand SQL Injection—not only for security experts but also for anyone involved in developing, managing, or protecting web applications.
What is SQL Injection?
In summary, SQL Injection is an attack that allows an attacker to compromise the SQL queries a web application interfaces with its database. SQL queries are used for communication purposes with databases and to pull back or update or delete records according to the request sent. In SQL Injection, the application takes data provided by the user, such as a form input, and injects it directly into an SQL query without proper validation. This vulnerability allows attackers to manipulate the query and perform unwanted commands on the database.
Example Scenario
Suppose the login form is developed specifically by the website administrators that asks for a username and password. In case of inappropriate validation for the input form on its direct submission to a SQL query, an attacker can add malicious SQL code in the input field. The code changes the behavior of the SQL query and may trick the system to reveal sensitive information or even bypass the authentication scheme.
SQL Injection is more than a bad coding practice; it is an actual vulnerability with devastating potential on any web application that uses SQL databases. They can gain access to users’ information, alter the contents of the database, or even take control of the server totally if not adequately protected. Therefore, the developers, as well as security teams, who try to keep their applications secure should know how SQL Injection works and place proper validation methods.
How SQL Injection Works (with Examples)
SQL Injection happens because of poor input handling in SQL queries. Since the input sanitization is poor for user inputs, it is possible to manipulate SQL syntax for a hacker to access unauthorized actions on a database. Here is an example of a simple SQL Injection attack process:
Suppose we have the SQL query below validating user credentials:
SELECT * FROM users WHERE username = 'user_input' AND password = 'pass_input';
This SQL statement should return only user records when both the username and password match the database values. But if the application does not sanitize its input data, an attacker could simply input this into the username field:
-
Username: admin’ —
-
Password: (left blank)
The SQL query would then look like:
SELECT * FROM users WHERE username = 'admin' --' AND password = '';
The — indicates that it’s an SQL comment, hence the password check is ignored. Now the query will return the admin user data without checking the password, so the attacker can possibly misuse the result.
This shows how SQL Injection can be present with something as simple as a login form. Advanced injections involve fetching particular data, updating tables, or deleting data. The ability to understand how this is done is vital in producing secure, safe web applications.
Types of SQL Injection
There are various types of SQL Injection, and each type brings with it different methods and levels of severity. Here are the categories with brief explanations.
In-band SQL Injection
This is the most common form, whereby the attacker uses the very same communication channel to inject the input and retrieve the data. In this case, if an application is leaking error messages, an attacker will manipulate the input such that SQL errors are generated. Consequently, the attacker will be exposed to some details concerning the structure of the database as well as other sensitive information.
Blind SQL Injection
In Blind SQL Injection, the attackers do not get direct feedback from the database. Instead, they infer the answer through mere changes in the behavior of the application. For instance, an attacker could send a query that would take a significant amount of time to process, which then leads to revealing indirect information, by virtue of it being processed.
Out-of-band SQL Injection
This type is not very common, and the database will accept more than one channel. In this case, attackers upload data to the database in one channel and download their results from another. This method is often resorted to when in-band or blind SQL injection cannot be carried out but still allows data to be extracted.
Understanding the type is key because every type has a different means of prevention and detection strategies. A comprehensive understanding of these differences will help the developers and security teams shield applications from diverse kinds of attack vectors.
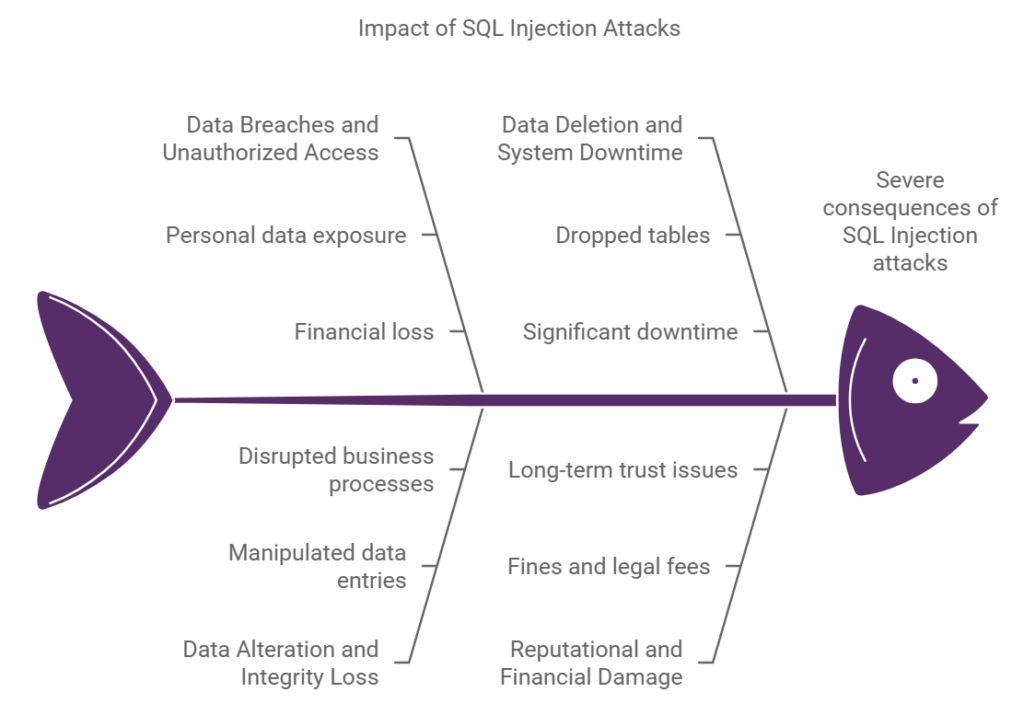
Impact of SQL Injection Attacks
SQL Injection attacks may lead to severe outcomes depending on data and privileges gained by attackers. Some of the main risks associated with SQL Injection include the following:
Data Breaches and Unauthorized Access
The first and most significant threat is unauthorized access to sensitive data. Personal data, credit card information, or login information can be compromised for identity theft and financial loss.
Data Alteration and Integrity Loss
The bad code injected into data may alter entries within the data, causing it to become corrupted. The manipulation may cause business processes to be altered, make data unreliable, or interfere with data-driven decisions.
Data Deletion and System Downtime
In some cases, SQL Injection allows hackers to drop tables or even the whole database. In doing so, it would result in significant downtime and loss of critical data. This consequently leads to significant disruptions and may also affect an organization’s reputation.
Reputational and Financial Damage
-
Loss of Customer Trust
-
Fines for non-compliance with regulations
-
Legal fees
SQL Injection may thus impact the bottom line of an organization and its reputation, making it take a longer period to regain trust from its customers.
All of these effects make strong security measures indispensable. Preventing SQL Injection is not just a technical job; it is basically what forms the very foundation of how trust can be maintained and assets under an organization’s control protected.
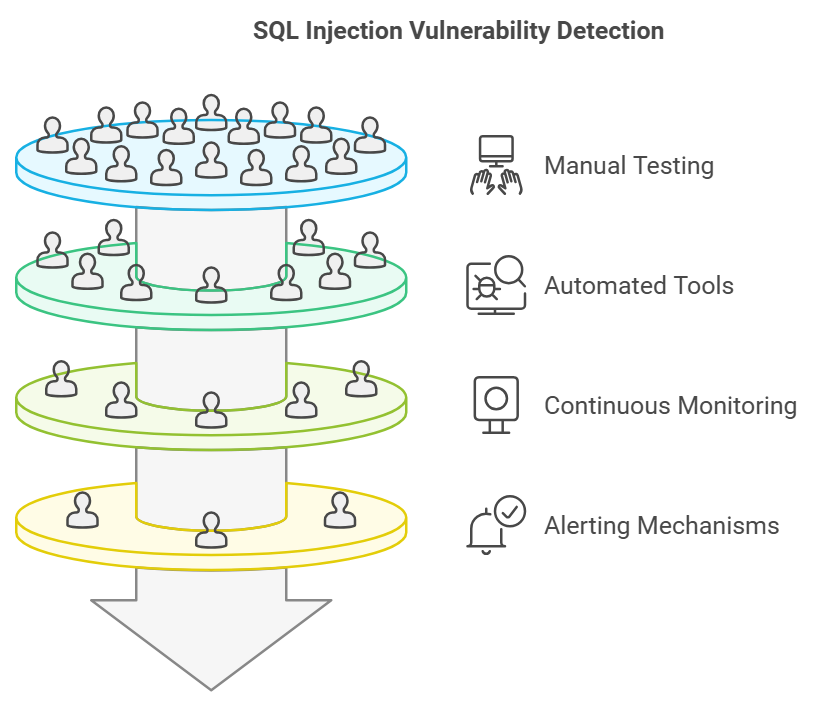
Detecting SQL Injection Vulnerabilities
To defend your applications from SQL Injection, it is highly important to detect vulnerabilities proactively. This is how you go about it:
Manual Testing
-
White-box Testing: One technique is manual input testing of inputs either by trying different SQL syntax, looking for anomalies in the outputs or whether the error messages contain database information. Such probing might uncover open input fields to help avoid an injection.
Automated Tools
-
SQLmap, Burp Suite, and OWASP ZAP: Automated tools available include SQLmap, Burp Suite, and OWASP ZAP, which automatically detect the occurrence of a SQL Injection attack. Such tools may simulate SQL Injection attacks, point out vulnerable areas, and suggest remediation measures.
Continuous Monitoring and Logging
-
Active Monitoring and Logging: Active monitoring and logging might detect abnormal patterns, such as unsolicited database queries or access attempts.
-
Alerting Mechanisms: Inform security teams of potential attacks in a real-time manner.
SQL Injection Vulnerability Detection will form the first layers of defense. The use of both manual as well as automated methods ensures that all vulnerable areas are covered in detail.
SQL Injection Countermeasures
Implementing effective countermeasures is essential to prevent SQL Injection. Key strategies include:
Parameterized Queries
Using parameterized queries, also known as prepared statements, treats user input as data, not executable code. Input will never become mixed up with SQL syntax in this manner, avoiding SQL injection.
Stored Procedures
Stored procedures encapsulate SQL logic, thus preventing direct access of SQL commands. No guarantee, but it does isolate user inputs from the SQL statements.
Input Validation
-
Validate and Sanitize All Inputs: Ensure inputs match the expected format. For instance, limit the input to be numeric fields only to inputs that expect only numbers, and do not have special characters in text fields.
Object Relational Mapping (ORM)
Use of ORM libraries such as Hibernate or SQLAlchemy abstracts SQL code hence reduces the amount of direct SQL handling thus decreasing SQL injection risks.
Web Application Firewalls (WAF)
Web Application Firewalls (WAF) analyze HTTP traffic and help detect and block SQL Injection attempts, providing a deeper layer of protection from attacks.
SQL Injection prevention involves good coding practices as well as proper use of external security tools, which would prevent it strongly.
Case Studies and Real-World SQL Injection Incidents
Many of the world-known organizations have fallen prey to SQL Injection attacks, proving the extent of vulnerability and hence how imperative it is to prevent it. There are a few examples listed below:
Sony Pictures (2011)
Attackers exploited a SQL Injection vulnerability that amounted to millions of records exposed, including sensitive user information. The breach adversely affected Sony’s reputation and highlighted how vulnerable poor database security could be.
TalkTalk (2015)
TalkTalk has recently faced one of the biggest data breaches reported in the UK when it became a victim of an SQL Injection attack that compromised thousands of customer personal information. This led to regulatory scrutiny and subsequent fines, clearly showing the critical costs of ignoring SQL security.
These instances prove that SQL Injection is not just a hypothetical risk—it has real consequences for companies of any size.
Tools for Testing and Prevention of SQL Injection
Utilizing specialized tools can streamline SQL Injection testing and prevention:
SQLmap
This is an open-source tool that automates the detection of SQL Injection. It supports several databases and injection methods, making it very suitable for security testing purposes.
OWASP ZAP
OWASP ZAP can be used to detect SQL Injection and other vulnerabilities within web applications. It is one of the widely used tools in security testing because of its ease of use and integration with various environments.
Burp Suite
This is a powerful tool used in penetration testing to carry out advanced scanning for SQL Injection and other web vulnerabilities.
All these can lighten the activities for SQL Injection testing, and thereby security teams will be able to identify and properly address vulnerabilities.
SQL Injection on Different SQL Platforms
SQL Injection is dependent on the SQL-based database. Here’s how it applies to some of the well-known databases:
MySQL
-
Vulnerabilities: General SQL Injection attacks.
-
Prevention: Use parameterized queries and escape special characters.
PostgreSQL
-
Vulnerabilities: Some injection methods are ineffective due to different input handling, but advanced SQL Injection is still possible if it’s not secured.
-
Prevention: Implement robust security measures tailored to PostgreSQL.
SQL Server
-
Vulnerabilities: SQL Server is vulnerable to injection.
-
Prevention: Utilize native stored procedures and parameterized queries to mitigate risks.
Understanding which risks are specific to your database type allows you to take educated steps in securing it in the right manner and making the application more resilient to SQL Injection.
Best Practices for Developers and Security Teams
Adopting best practices can significantly reduce the risk of SQL Injection:
Code Reviews and Security Audits
Conduct thorough code reviews to catch SQL Injection vulnerabilities early.
Security Patches
Keep software up to date with the latest security patches to protect against known vulnerabilities.
Education and Awareness
Educate teams on SQL Injection risks. This sets the organization towards a security-first mindset within development practices.
These best practices minimize the chances of SQL Injection vulnerabilities and foster a security-aware culture in the organization.
Conclusion
SQL Injection is an extremely common threat which can potentially destroy web applications if not taken care of properly. Awareness of SQL Injection mechanisms, identification of various types of attacks, and careful prevention methods can protect developers and security teams from common vulnerabilities.
In today’s digital world, sensitive data protection is very important, and preventing SQL Injection would be part of that process. Having completed the steps and tools found in this guide, you will have secured your applications and safeguarded your organization’s reputation and assets.