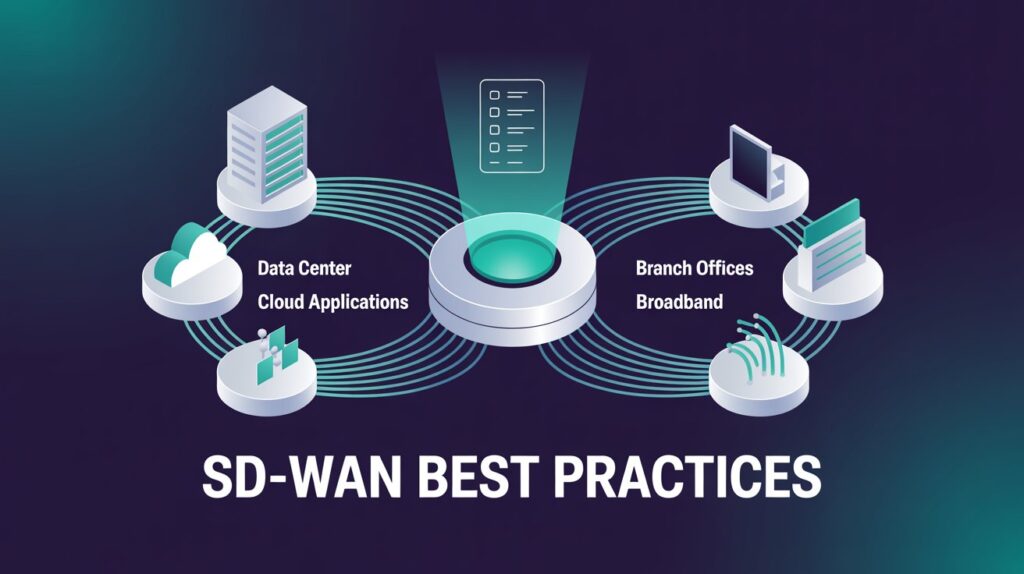
Top 10 SD-WAN Best Practices Every IT Team Should Follow
Remember when all of your branch traffic rode an expensive MPLS back-haul to one lonely data center? Those days are long gone. Today, cloud apps, hybrid work, and video-everywhere demand a WAN that’s agile, secure, and cost-smart. Software-Defined WAN (SD-WAN) answers that call—but only if you run it well. Misplaced policies or sloppy failover settings […]
Top 10 SD-WAN Best Practices Every IT Team Should Follow Read More »