Imagine this: You’re sending a love letter to someone, but you’re forced to send it through a crowded, untrustworthy post office. Scary, right? What if anyone could read it before it reaches your intended recipient? Now, replace that love letter with your bank details or private conversations. This is what the internet used to be like before public-key cryptography swooped in like a superhero to save the day.
Let’s unravel the story of how public keys work their magic, why they matter, and the small yet mighty role they play in keeping your digital life secure.
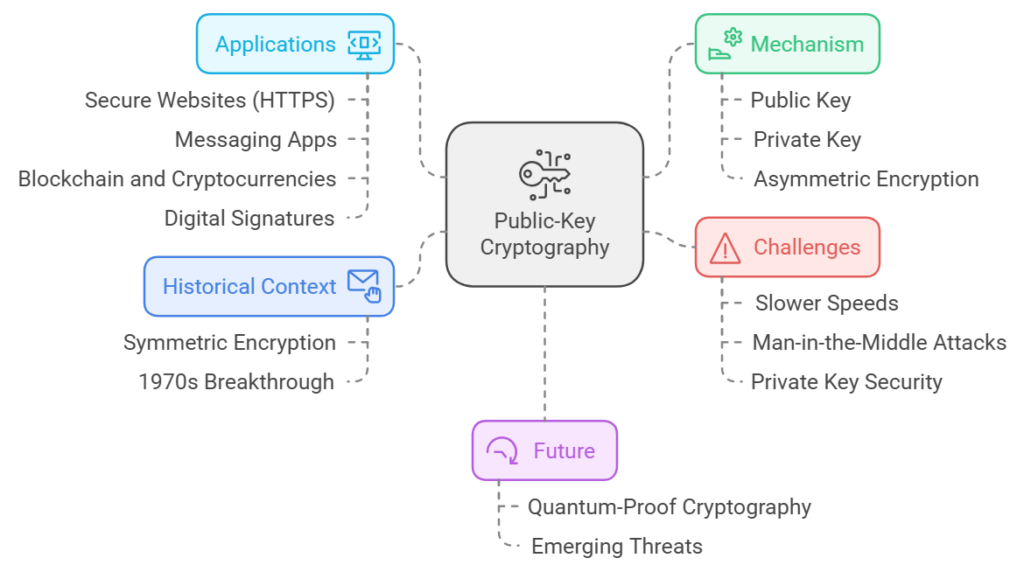
A World Without Secrets
Before public-key cryptography, the world relied on something called symmetric encryption. This meant both the sender and receiver used the same key to encrypt and decrypt messages. Sounds simple, right? But here’s the catch: what if the key itself was stolen during transmission?
Think of it like sharing a locker key with a friend. If someone intercepts the key, they have access to everything inside. For decades, this was the Achilles’ heel of online communication. People had to trust others with their keys, and let’s be honest—trust is a luxury in the digital world.
But, in the 1970s, researchers stumbled upon a groundbreaking idea: What if you didn’t need to share the key at all? Enter the concept of public-key cryptography, a system that transformed the way we think about security forever.
What is a Public Key, and Why is It So Special?
Okay, so here’s the deal. A public key is part of a pair. It works hand-in-hand with its secret sibling: the private key. Think of the public key as your home’s address. Anyone can know it, use it, and send stuff to you. But only you, with your private key (your front door key), can access what’s inside.
Here’s why this is genius:
-
You can share your public key with the world without worrying about security.
-
The private key stays with you, hidden and safe.
But, how does this actually work? Let’s say you’re buying something online. The website gives you its public key. You use it to encrypt your payment details. Even if someone intercepts the message, they can’t decode it without the private key.
Therefore, your data stays safe, and trust is built. Neat, isn’t it?
The Inner Workings of Public Keys
Let’s get a bit nerdy for a second. Public keys are part of a system called asymmetric encryption, and here’s how it works:
-
You encrypt a message using someone’s public key.
-
They decrypt it using their private key.
-
It’s a one-way process—your private key never gets involved.
But, there’s a twist. Public keys aren’t just for encrypting messages. They’re also used for authentication.
Picture this: You’re trying to verify if a message claiming to be from your bank is legit. The bank uses its private key to “sign” the message, and you use their public key to verify it. If the public key matches the signature, it’s authentic.
But, here’s the catch: If someone manages to fake the public key, they can trick you into believing a forged message. Scary, right? Therefore, we have systems like Certificate Authorities (CAs) to validate public keys and keep the system honest.
Public Keys in Action
Let’s take a step back and look at how public keys quietly work behind the scenes to protect your daily activities:
-
Secure Websites (HTTPS): Ever noticed the padlock icon in your browser? That’s public-key cryptography in action. Your browser uses the website’s public key to encrypt your data before sending it.
-
Messaging Apps: Apps like WhatsApp and Signal use public keys to create secure, end-to-end encrypted chats. Only you and the recipient can read the messages—no one else, not even the app developers.
-
Blockchain and Cryptocurrencies: Public keys serve as wallet addresses in cryptocurrencies like Bitcoin. When someone sends you money, they use your public key. Only you, with your private key, can access the funds.
-
Digital Signatures: Imagine downloading software. How do you know it’s authentic? Developers use public keys to let you verify the software hasn’t been tampered with.
Public keys are everywhere, silently safeguarding your online life. But, do you ever stop to think about them? Probably not.
The Challenges (Every Hero Has a Weakness)
Public keys are powerful, but they’re not perfect. Let’s talk about the bumps in the road:
-
Slower Speeds: Public-key cryptography is computationally heavy. Encrypting large amounts of data? Not the best option. That’s why it’s often combined with faster symmetric encryption for efficiency.
-
Man-in-the-Middle Attacks: Remember the trust issue? If someone intercepts and replaces a public key with their own, they can decrypt your messages. Therefore, certificate authorities are crucial to prevent such attacks.
-
Private Key Security: The entire system falls apart if the private key is stolen. Imagine losing the key to your treasure chest—it’s game over.
Why Public Keys Matter Now More Than Ever
Let’s pause for a moment. Think about the digital world we live in today: Online shopping, remote work, streaming services—all of this relies on secure communication.
But, with the rise of cyberattacks, staying secure has become more challenging. Hackers are getting smarter, and traditional methods won’t cut it. Therefore, technologies like quantum-proof public-key cryptography are being developed to tackle emerging threats.
Public keys are evolving, ensuring they stay one step ahead in the race for security.
What’s the Big Takeaway?
Public keys may be invisible, but they’re the backbone of modern digital security. They’re the reason you can shop online without worrying about stolen credit card details or chat freely without fearing eavesdroppers.
And here’s the kicker: public keys are simple yet incredibly powerful. They prove that sometimes, the quietest tools make the loudest impact.
So the next time you see a padlock on your browser or hear about encryption, remember the unsung hero working tirelessly to protect you: the humble public key.
Now, isn’t it time we gave this superhero its due credit?