Encryption is one process that can transform readable data, referred to as plaintext, into a coded format or ciphertext so that nobody except the owner can read the data. Only through proper possession of the decryption key can it recover the data, thereby ensuring its secrecy and integrity.
Think about it: data breach losses estimated at $4 billion worldwide in 2023 alone. Encryption thus is a vital asset for securing private information away from the wrong parties.
This is a comprehensive guide to getting to know encryption. Being a technology enthusiast, a business owner, or simply the curious type, you’ll get valuable information on how it works, its diverse forms, applications, and future developments. After reading this guide, you may come to appreciate just how important encryption will be in safeguarding our lives in this digital age and be well-equipped with knowledge on putting robust encryption into practice.
Encrypted History
Ancient Forms of Encryption
Encryption dates back thousands of years, with one of the most ancient known encryption methods being the Caesar Cipher—a type of simple substitution cipher, where Julius Caesar protected his military communications. It simply involved shifting every letter in the plaintext by a fixed number down the alphabet, which at the time successfully hid the messages from unintended receivers.
Jumping forward to World War II, the Enigma Machine catapulted encryption to new levels. Utilized by the German military, the Enigma Machine consisted of a series of rotors and wiring configurations that enabled complex substitution ciphers. Of course, this was unbreakable encryption until the Allied cryptanalysts, particularly Alan Turing, broke its codes and thus turned the tide of the war.
Contemporary Encryption History
It is the post-war era, which saw mechanical to mathematical encryption methods in place. Encryption algorithms during the computer era became so complex that they relied much on the use of various complex mathematical functions for securing information. With the dawn of the 1970s and the development of public-key cryptography, where asymmetric keys came into vogue, this revolutionized encryption. This was considered to provide higher security to the encryption system and enable secure key exchange over even unsecured channels.
As the digital dawn began to open up through the Internet, encryption became a primary need for protecting communications, transactions, and personal data online. It does not seem unusual today to see modern encryption algorithms such as Advanced Encryption Standard (AES) and Rivest-Shamir-Adleman (RSA) at the heart of all digital security purposes.
How Encryption Works
Basic Principles
At its core, encryption transforms plaintext—that is, readable data—into ciphertext: an encoded version that, to a human eye, appears to be some sort of random character string. The encryption key is a bit-string that determines the output of the encryption process. Without the decryption key, the ciphertext cannot be decoded back into plaintext.
Encryption Algorithms
Encryption algorithms are mathematical procedures describing how plaintext is transformed into ciphertext. They can be broadly classified into two groups:
-
Symmetric Algorithms
-
They utilize the same key for decrypting and encrypting. Examples include AES and DES.
-
-
Asymmetric Algorithms
-
They use a pair of keys—a public key for encryption and a private key for decryption. Examples include RSA and ECC.
-
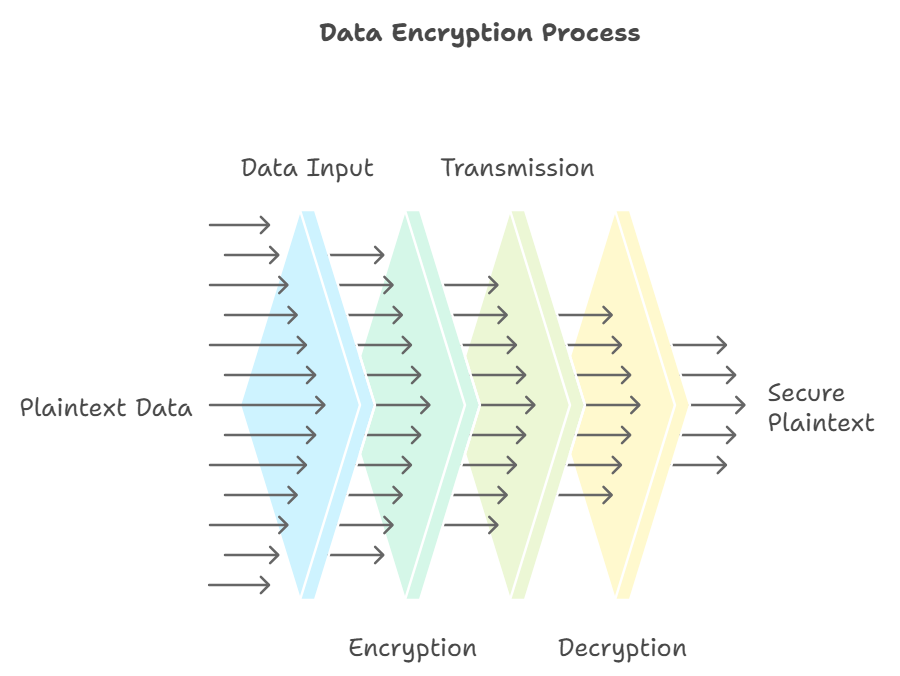
Encryption Process
-
Data Input
-
The sender has plaintext data that he or she wants to safeguard.
-
-
Encryption
-
The plaintext is replaced by the ciphertext using an encryption algorithm and a key.
-
-
Transmission
-
The ciphertext is transmitted to the recipient over a probably insecure communication channel.
-
-
Decryption
-
The recipient decodes the ciphertext using a decryption key to recover the plaintext of the original information.
-
Thus, if the data being transmitted was intercepted, it would be meaningless without the correct key.
Types of Encryption
Symmetric Encryption
This symmetric encryption algorithm utilizes a single key, used in encryption and decryption. This is a good encryption scheme if the amount of encrypted data is large because it is simple and fast.
Advantages:
-
Performs much faster compared to asymmetric encryption.
-
Ideal for bulk data encryption.
Disadvantages:
-
Key distribution is difficult; securely sharing the key among parties will be necessary.
-
If the key is compromised, the security of the encrypted information becomes compromised.
Common Uses: Protect data at rest, such as files on a hard drive or data on a database.
Examples: AES, DES, Triple DES.
Asymmetric Encryption
Asymmetric encryption is also known as public-key encryption. It uses a pair of keys; for encryption, the public key is used and for decryption, the private key is used.
Advantages:
-
Separation of keys for greater security; the public key can be distributed publicly, while the private key is kept secret.
-
It allows for secure key exchange over open channels.
Drawbacks:
-
Much slower than symmetric encryption.
-
Poor for encrypting big data.
Advantages:
-
Secure key exchange, digital signatures, and encryption of small data transmits.
Examples:
-
Rivest–Shamir–Adleman (RSA)
-
Elliptic Curve Cryptography (ECC)
-
Diffie-Hellman key exchange
Hybrid Encryption
Hybrid encryption combines the good features of symmetric and asymmetric encryption. The most frequently used approach is to use asymmetric encryption for securely exchanging the symmetric key that then encrypts most of the data.
Advantages:
-
Both security and performance are balanced.
-
The key is distributed very securely but the encryption of the data remains very efficient.
Common Use: SSL/TLS protocols are used in secure web communications.
Examples: Secure Socket Layer (SSL), Transport Layer Security (TLS).
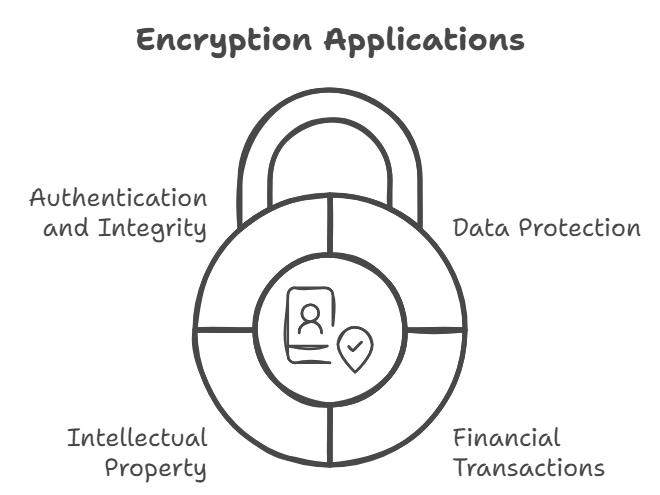
Applications of Encryption
Data Protection
Encryption of Information While data encryption helps prevent unauthorized access to information from rest and in transit scenarios, it also performs numerous other important functions.
-
In Rest: Encryption of Data on Devices, Servers or in the Cloud
-
Encrypting information on devices or servers or in the cloud prevents unauthorized access in cases of a data breach or theft of a device or server.
-
-
In Transit: Encrypting data as is transmitted over networks, for instance, when HTTPS is being used with web traffic means that the information between sender and receiver is protected.
E-mails and Messaging: Pretty Good Privacy (PGP) and Signal tools encrypt the content of communications, making them unavailable to access through eavesdropping.
Virtual Private Networks (VPNs): VPNs encrypt internet traffic, thus ensuring safety online; at times, while surfing on public Wi-Fi networks, by creating a private tunnel for data transmission.
Financial Transactions
Encryption is the core basis for secure financial activities
-
Online Banking Security: Encrypts sensitive financial information, thereby protecting transactions with identity theft and fraud.
-
E-commerce: Secure payment processing that safeguards your credit card information and personal data during online transactions.
Intellectual Property
Companies encrypt their assets
-
Business Data: It helps to protect secrets and trade secrets and proprietary matters, as well as strategic plans from competitors and unauthorized parties.
-
Personal Data: To protect sensitive personal information including social security numbers, medical records from illegal access or exploitation.
Authentication and Integrity
Encryption technologies also provide data authenticity and integrity.
-
Digital Signatures: Use encryption to verify messages or documents, ensuring that those documents have not been modified during their transmission.
-
Certificates: They establish online identities and authenticate links. The certificates are an important part of HTTPS, apart from other secure services.
Role of Encryption
Privacy Protection
Encryption is the basis for any privacy within a digital setting.
-
Individual Privacy: Defend your personal data against any unauthorized access. Here, privacy defends against disclosure of personal communications, financial details, as well as sensitive documentations.
-
Corporate Privacy: The data remains private to businesses. This means that the competitive and the industrial espionage are safeguarded.
Improvement of Security
In addition to privacy, encryption goes along with general security immensely.
-
Cyber Threat Mitigation: It eliminates risks based on data compromise, man-in-the-middle attacks, and identity theft because stolen data loses its meaning without the decryption key.
-
Data Integrity: It ensures data is not changed as it moves and is stored in ways that unauthorized parties do those changes.
Rules Compliance
Encryption has to be adopted in many industries while having a solid understanding of data protection laws and regulations.
-
GDPR, HIPAA, etc.: Encryption lets organizations comply with General Data Protection Regulation (GDPR) and Health Insurance Portability and Accountability Act (HIPAA), which require keeping every personal and sensitive information safe.
-
Industry Standards: Most industries have specific security standards when it comes to encrypted documents, for example, the Payment Card Industry Data Security Standard (PCI DSS) on financial transactions.
Building Trust
This implementation of encryption builds trust with the user and customers.
-
Consumer Confidence: Indicates a company that cares to protect a consumer’s information, hence building trust for consumers and service providers.
-
Corporate Reputation: A sound security posture, founded on effective encryption, assists in building corporate reputation as well as credibility in the marketplace.
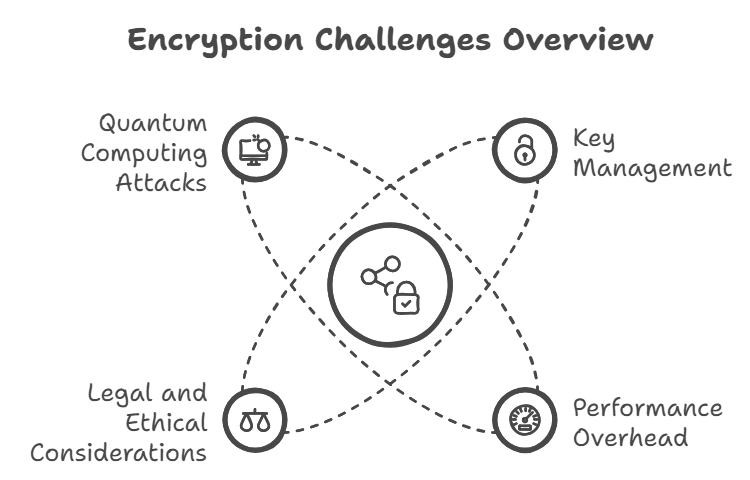
Challenges and Issues
Key Management
Secure encryption demands proper management of keys.
-
Key Generation and Distribution: Keys need to be created in ways that are reliably secure as well as distributed in a manner that access cannot be gained by unauthorized parties.
-
Storage and Rotation: Secure storage solutions, such as Hardware Security Modules (HSMs), are the only option. The rotation of keys should be regular so that there is a lesser chance of being betrayed by a key.
Performance Overhead
Encryption is undoubtedly the security advantage but it’s not without a performance overhead.
-
Effects on Systems: Although encryption and decryption are of high utility in terms of supplying safety control, these processes do consume some amount of computational resources and hence tend to slow systems, primarily when working with large datasets or high-throughput environments.
-
Optimization Techniques: A few techniques include hardware acceleration, optimization of the algorithms used, and balancing encryption strength with the need for performance might reduce overhead.
Legal and Ethical Considerations
Encryption use does intersect with legal and ethical considerations.
-
Government Access: Whether a government has the right to backdoor access for encrypted data in the interests of legitimate investigation is a constant source of debate, which pits national security requirements against individual rights to privacy.
-
User Privacy vs. Security Requirements: User privacy is always at variance against the requirement of compromise made to security concerns.
Quantum Computing Attacks
Quantum computing advancements are sure to shake existing encryption methods.
-
Attacks: Quantum computers can potentially attack widely used encryption algorithms and render them useless.
-
Readiness for the Future: Developing quantum-resistant encryption algorithms is the need for future data security.
Future of Encryption
Post-Quantum Cryptography
As quantum computing comes along, so should encryption methodologies.
-
New Algorithms: Designing algorithms that have quantum resistance so that encryption becomes secure in the quantum era.
-
Recent Research and Developments: The standardization of post-quantum cryptographic algorithms is being taken up by institutions like the National Institute of Standards and Technology (NIST) to replace the vulnerable ones.
Homomorphic Encryption
Homomorphic encryption is a method that enables computations on ciphertext without decryption.
-
Improving Privacy in Data Processing: Provides secure analysis and processing of data in the cloud while keeping the underlying data private.
-
Applications and Advantages: Allows privacy-preserving data mining, secure voting systems, and confidential machine learning models.
Blockchain and Decentralized Systems
Encryption is an essential component of the functionality and security capabilities of blockchain and decentralized systems.
-
Transaction Encryption: Ensures the non-repudiation of transactions, further ensuring the integrity of the blockchain ledger to itself.
-
Maintenance of Integrity and Trust: Encryption forms the underpinning of consensus mechanisms and ensures that no unauthorized alterations occur to a blockchain.
Advanced Encryption Techniques
Advancements in encryption techniques are pushing data security to unrelenting horizons.
-
Zero-Knowledge Proofs: One party can prove to another that a statement is true without revealing any additional information, which enhances privacy without compromising security.
-
AI and Machine Learning in Encryption: Use artificial intelligence to develop better, smarter, adaptive encryption that can respond in real-time to evolving threats.
Implementing Encryption Best Practices
The Right Encryption Technique
The choice of encryption technique will provide the foundation for security in data.
-
Determining Needs: There are specific use cases, data sensitivity, and performance requirement determination for whether symmetric, asymmetric, or hybrid encryption is most suitable.
-
Up-to-date: Be aware of current and developing standards in encryption and ensure that the encryption method chosen is secure against new threats.
Compensating Control Secure Key Management
Good key management is key to effective encryption.
Best Practices:
-
Use strong, cryptographically random keys.
-
Use hardware-based secure key storage like HSMs.
-
Rotate keys periodically to reduce the impact of possible compromises.
Tools and Solutions: Implement specific Key Management Systems (KMS) that employ automated key generation, storage, rotation, and controls.
Continuous Audits and Scans
Ongoing encryption audits ensure that encryption remains always on and complies with many regulatory demands.
-
Encryption Audits: Security audits ought to be conducted regularly as a method of assessing encryption strength and activities implementation.
-
Checking Encryption Compliance: Encryption ought to strictly adhere to applicable regulations and the latest industry standards. Areas to be rectified will be ascertained by such encryption audits.
Stakeholder Awareness Raise
Awareness and education are integral parts of an encompassing encryption strategy.
-
Training Your Employees: Educate the employees about how critical encryption is, the right management of keys, and security which prevents human error from breaching data.
-
Creating Awareness: Protecting data through encryption across the organization while instilling the importance of the roles of the stakeholders in the organization.
Conclusion
Encryption can be considered a highly effective tool in the digital world with regard to data protection at rest and on the move. Since this form of encryption changes plaintext into ciphertext based on some algorithms or keys, the information must not be accessed or acquired incorrectly and kept confidential. Its applications range from simple ciphers, covering plenty of tasks such as secure communication, financial transactions, and protection of data, and evolve according to new security issues and technologies emerging.
This has a bearing on what occurs in our private and professional lives as we increasingly become dependent on digital technologies. Encryption serves more than to guard us against cyber threats—also underlying trust and integrity is the reason it has been recognized as necessary for legitimate digital interactions. Indeed, the field of encryption is likely to experience an even more fundamental change due to the new technologies of quantum computing and others which are likely to raise new requirements for innovations in encryption.
Encrypt to Secure Your Digital Life
Take the time to know and apply appropriate encryption. It may be for personal information, business information, or governmental compliance, but proper encryption is one of your best lines of defense against unauthorized access and cyber threats. Take action today:
-
Implement Strong Encryption: Identify your data security needs and apply an appropriate mechanism for encryption.
-
Secure Keys Management: Invest in strong key management solutions to safeguard your encryption keys.
-
Keep Yourself Up-to-Speed: Track encryption trends and progressions so that you stay ahead of the security game.
-
Educate Yourselves and Others: Foster a security-aware culture, both inside and outside of your organization’s walls.